At one time, enterprise security could be considered a perimeter surrounding an organization. Data remained largely within the organization’s sites and could be protected from unauthorized access by firewalls, virtual private networks (VPNs), and physical barriers. Even when data began to be accessible beyond the organization using Internet websites and portable devices, the company still owned and managed these potential attack vectors.
The assets an organization needs to protect, sometimes called its digital estate, have grown enormously in recent years, and so have the enterprise’s means of ingress and egress. This digital estate certainly includes the company’s data, but it also includes the users who access the data and the systems and devices by which they access it. All three of these assets are potential weak points in an enterprise security system, and all three need protection (see Figure 3-37).
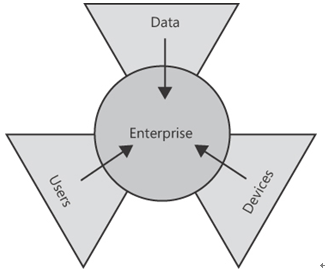
FIGURE 3-37 The enterprise asset types needing protection
The commitment to the cloud required by adopters of Microsoft 365 creates a new attack vector. However, to fully protect the company’s data, IT administrators now have to be concerned with the cloud, and they must be concerned with security for devices that are not directly owned by the organization, not located within the organization, and, in some cases, owned by users who are not even employees of the organization.
Therefore, the primary storage for an organization’s data can be located in the cloud or on servers kept on-premises. In many cases, the data is split between the two. That means administrators must be responsible for the security of both. However, in addition to the primary storage locations, the devices workers use to access the data are also potential attack vectors. The increasing adoption of the BYOD paradigm complicates the process of securing data that might be stored in someone’s pocket on a device that might not be fully manageable by enterprise administrators.
The security problem also extends beyond the logical extremities of the enterprise to the partners, clients, and consultants with which employees share data. These people use their own systems and devices that are even farther out of reach of the enterprise administrators. All these attack vectors can provide intruders with a way into the enterprise network, and once sophisticated intruders are inside, they often manage to stay there and extend their influence.
While there are always a certain number of casual cybercriminals who are relatively easy to repulse, the serious, professional penetration attempts that often afflict large enterprises can be incredibly sophisticated and take place over long periods of time. Microsoft 365 includes a powerful array of security tools that allow administrators to implement various types of protection over the company’s data and the devices that access it, but these tools are not simple turnkey solutions. Enterprise administrators must design a security plan that prioritizes the sensitivity of the company’s data, assesses the vulnerability of the systems and devices on which the data is stored, identifies the users and their data needs, and specifies how the Microsoft 365 tools will be used.
These complicating elements in today’s enterprise networks—such as remote users and BYOD policies—call for a rethink of the perimeter security model. The original principle was to keep all potentially dangerous elements outside the network perimeter—or near the perimeter—in a secure subnet. These days, the potential dangers are everywhere, both inside and outside the network perimeter, and a more comprehensive approach is needed.
For example, in the traditional network security architecture, the assumption is that anyone authenticated and allowed inside the perimeter (physically or virtually) is considered a trusted user and needs no further validation. In the modern business world, this is certainly not the case. Threats can be present inside the perimeter and can even originate from validated users within the organization itself, whether those users are malicious or merely gullible. This is why the new security model currently gaining acceptance is called Zero Trust.
Zero Trust is a security architecture based on the principle of “never trust, always verify.” Simply put, all requests, devices, and users must be authenticated and authorized every time they attempt to access a protected resource. Even on-premises employees who have already been authenticated while logging on to the network will continue to be verified whenever they access protected network resources.
The fundamental principles of a Zero Trust environment are as follows:
- Verify explicitly Identity verification is a continual process for every attempt to access a protected resource at every level, including identity, location, device condition, and data sensitivity.
- Use least privileges The least privileges concept calls for users to start with no access to the network at all and then receive privileges for the resources they require to perform their jobs. Users are granted access only to the resources they need (called Just-Enough-Access, or JEA), and for only the length of time they need it (called Just-In-Time or JIT access).
- Assume breach Every access request is assumed to be that of an attacker who has already penetrated the network and is attempting to move laterally within it to access other protected resources. By comparing current user activity with known attack behaviors, Microsoft 365 can contain genuine attacks by restricting them to a limited part of the network.
Due to outside events, the evolution of the modern enterprise network has been forced to accelerate in recent years. Because many more people work remotely and use personal devices to access company data, location-based security architectures like the traditional network perimeter are no longer practical. The Zero Trust architecture no longer relies solely on users’ locations to determine their trustworthiness.
Compared to the perimeter model, which authenticates users only once and then trusts them until they log off, the Zero Trust model calls for users to be authenticated and authorized constantly as they move about within the network and access different resources.
Zero Trust is not an application, service, or Microsoft 365 feature. Rather, it is a philosophy administrators can apply to their network’s security posture design. All organizations have to assess their security needs and the threats they face. Zero Trust focuses on six critical security areas, as shown in Figure 3-38, each of which administrators should consider in their planning.
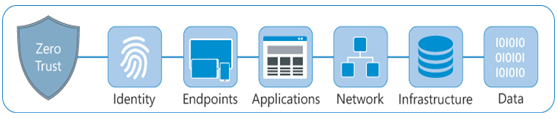
FIGURE 3-38 Six security criteria of the Zero Trust architecture
The six security criteria central to the Zero Trust security architecture are discussed in the following sections.







Leave a Reply