Microsoft Defender for Identity, formerly known as Azure Advanced Threat Protection (Azure ATP), is a product that protects the identities stored in Active Directory. There was at one time a separate Defender for Identity management portal, but the interface has now been integrated into the Microsoft 365 Defender portal.
Defender for Identity monitors the Active Directory communications involved in identity creation, management, authentication, and authorization and creates a profile of each user’s identity-related activities. The signal is then sent to Microsoft 365 Defender, which collates it with the signals from the other Defender products, as shown in Figure 3-22, to create a comprehensive picture of any attacks that occur. The identity information gathered by Defender for Identity is a crucial contributor to the overall security context developed by Microsoft 365 Defender.
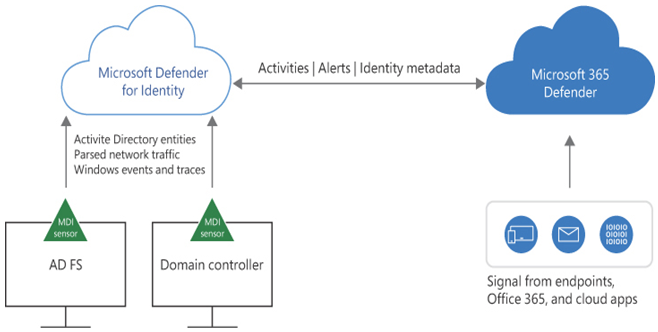
FIGURE 3-22 Microsoft Defender for Identity architecture
Defender for Identity also helps administrators reduce the existing identities’ attack surface by generating reports that suggest configuration best practices and identify potential weaknesses.
Defender is also aware of the tendency of attackers to attempt to compromise low-privilege identities and then move laterally within the network to gain access to more sensitive information. By detecting identities that have been compromised and analyzing the signals generated by Active Directory, Defender for Identity can track these lateral movements and identify other accounts that might have been compromised.
One of the biggest problems for IT security personnel in the enterprise is the overabundance of alerts, particularly in identity security. For example, every sign-on failure can generate an alert, which might result from an attempted attack or just a misspelled password by a user. Defender for Identity’s analytical capabilities helps reduce the number of alerts brought to the attention of administrators by identifying only those relevant to the network’s attack posture and creating a detailed attack timeline that omits the irrelevant.







Leave a Reply