The third element of the digital estate that must be considered when creating a risk management plan is the people who actually access the data. Whether deliberately or inadvertently, users are a constant vulnerability—if not an actual threat—to the organization’s data. After quantifying the organization’s information assets and their value and inventorying the hardware used to store, access, transmit, and process the information, the next step is to list the people with access to the information.
The people with access to the organization’s information certainly include employees authorized to create, view, and modify the data. However, a risk management team must also consider the possibility of other individuals accessing the data. Anyone with physical access to computers on which data is stored or from which it is accessible is a potential threat. This includes cleaning and maintenance staff, repair people, and even security guards. Even if an individual doesn’t have the credentials needed to sign on to a computer, it is still possible for a person to steal or destroy the computer or remove a hard drive from it.
A risk management plan should include a list of everyone with access to sensitive information and what exact information they can access. Following the Zero Trust philosophy, access control policies should be designed to provide users with permissions only for the data they need and no more. Administrators often do this within the organization by defining roles, granting the roles access to the required data, and then assigning individuals to those roles. This simplifies the process of authorizing new users, moving users to other jobs, and deauthorizing departing users. Then, administrators can create an orderly lifecycle for each user’s identity, as shown in Figure 3-62.
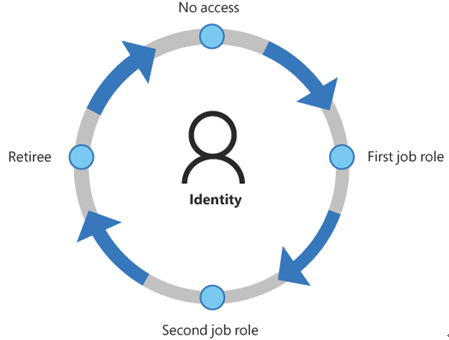
FIGURE 3-62 Identity lifecycle for an individual user
Every person who is granted access to company data should have an individual user account, including people who are working on-site temporarily. Any convenience that might be realized by creating generic guest accounts and assigning them to temporary users as needed will be nullified by the difficulty these accounts can cause when investigating an incident involving data loss or unauthorized access.
The plan must also include the means of ensuring that the individuals signing on to computers are actually the people they purport to be. Password policies can ensure that users create sufficiently long and complex passwords and change them regularly. Microsoft 365 also includes several enhanced authentication mechanisms, including multifactor authentication options calling for a fingerprint scan or a code sent to a mobile phone in addition to a password.
Users with administrative privileges present a greater potential threat to company data. The risk management plan should include policies requiring administrators to use standard user accounts for all typical work functions and administrator accounts only for tasks requiring additional privileges. This helps protect the company data from accidental damage or deletion and reduces the possibility of unauthorized software installation, whether intentional or not. Privileged access user accounts should have their own lifecycle policies with more stringent monitoring and control, as shown in Figure 3-63.
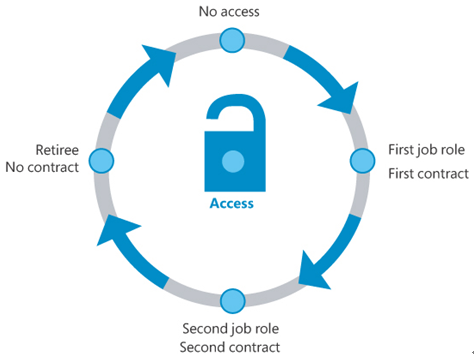
FIGURE 3-63 Lifecycle for a privileged access user account
Of course, even authorized users can be a threat, and the risk management plan should define the specific means by which new employees are vetted, including national (or international) background checks, credit histories, and confirmation of degrees and other credentials. For organizations working with extremely sensitive data, more extensive investigation of new hires might be in order.
Internal users are a major source of security incidents, although the incidents can be unintentional or deliberate. Disgruntled workers and industrial espionage are certainly legitimate causes of data theft or loss. However, simple slips, such as leaving a signed-on computer unattended, can be equally dangerous. In addition to addressing malicious threats, a risk management plan should devote sufficient attention to accidental threats.







Leave a Reply