All the security functions applying to the other five Zero Trust criteria essentially protect the organization’s data—its most valuable resource. Administrators must consider the data’s security in all possible states: in-motion, at-rest, and in-use. Depending on the nature and sensitivity of the data, each state might require different security measures. Microsoft 365 supports tools that can label, classify, and encrypt data to protect it in all states, such as Data Loss Prevention (DLP) and Azure Information Protection (AIP).
The traditional method for securing documents is to apply access control permissions to them. Permissions take the form of access control lists that are stored as attributes of individual files and folders. An access control list (ACL) consists of multiple access control entries (ACEs), each of which specifies a security principal, such as a user or group, and the permissions that grant the principal a degree of access to the file or folder.
Permissions have been around for decades, enabling users and administrators to restrict access to particular documents, but they must be applied manually and are difficult to manage for a large document collection. Someone also must keep track of which documents contain sensitive information that requires additional protection.
Therefore, Microsoft 365 includes security mechanisms, such as Azure Information Protection (AIP) and Data Loss Prevention (DLP), which can protect documents in other ways. The process of identifying documents containing sensitive data and securing them consists of the following four steps:
- Discovery The process of locating documents that contain sensitive information, either by automatic detection based on established data patterns or by prompting users to apply classification labels
- Classification The application of labels to documents containing sensitive information, indicating what types of protection should be applied to them
- Protection The application of specific security mechanisms to documents based on the classification labels that have been applied to them
- Monitoring The process of tracking document access trends, activities, and events and taking action when necessary
The process of discovering documents containing sensitive information is highly dependent on three factors:
- The nature of the organization
- The type of business in which the organization is engaged
- The policies or regulations with which the organization must comply
Tools like Data Loss Prevention have preconfigured sensitive information types that enable the automated discovery of documents that contain common data patterns, such as credit card and Social Security numbers. Also, administrators can create customized sensitive information types that can discover documents containing specific industry-based keywords and data patterns.
Like a physical label, the sensitivity labels applied by tools like AIP and DLP can warn users that a document contains sensitive information and recommend that users take certain actions. The labels persist with the documents as they travel to different systems and are opened in other applications—even on other computing platforms. However, AIP and DLP labels can also be configured to apply various types of protection, like those shown in Figure 3-42. The labels can
- Cause documents to be encrypted—at rest and in transit
- Be limited to use with specific applications
- Be restricted to specific users or devices
- Be configured to expire
- Be deleted after a specified lifespan
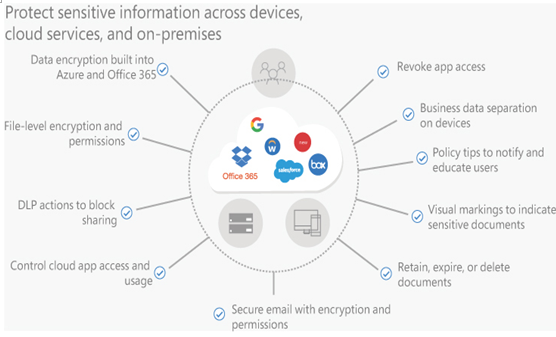
FIGURE 3-42 Microsoft 365 document protection mechanisms
Once the document classification and protection phases are complete, administrators are still responsible for monitoring the reports and alerts generated by the security tools. For example, repeated attempts to access or share protected documents by the same user or device can indicate the presence of a security breach, even if the attempts fail. The monitoring process should also include remediation so that an administrator who notices anomalous behavior can intervene by revoking document access privileges or quarantining files.







Leave a Reply