Companies often generate vast amounts of data with varying levels of sensitivity. It is usually not practical for an organization to implement the ultimate level of security over its data, so it is necessary to classify the information according to its function and value. Therefore, the risk management process should begin with an inventory of the organization’s information assets and a determination of each asset’s value to the company, considering its need for confidentiality, integrity, and availability. The factors to consider when compiling such an inventory are shown in Table 3-5.
TABLE 3-5 Risk factors for asset inventory
| Risk factor | Description | Example |
| Confidentiality | Access and disclosure of sensitive information by unauthorized persons | What if users’ passwords or Social Security numbers were stolen? |
| Integrity | Modification or damage of sensitive information by unauthorized persons | What if the company’s payroll information or product designs were changed? |
| Availability | Prevention of access to sensitive information by authorized users | What if the company’s client list or website was rendered inaccessible? |
The definitions used for information types will be specific to the nature of the business and their value to the business. For example, an attack that renders the site unavailable for several days would be inconvenient for a company that uses its website to provide customer support information. For a company that sells its products exclusively on the web, however, the unavailability of its e-commerce website for several days could be economically disastrous.
For a large enterprise, this type of asset inventory is typically not the exclusive province of the IT department. It will likely require the involvement of personnel from various departments and at various levels of the organization, including management, legal, accounting, and even clients and partners outside the company.
The value of an information resource might not necessarily be expressed in monetary terms. A data threat might result in lost productivity, the creation of additional work to restore or re-create the data, fines or penalties to the government or regulating agencies, or even more intangible effects, such as bad public relations or lost customer confidence.
The best practice to quantify the inventoried assets is to create a graduated scale considering all the risk factors particular to the business. A general numerical scale from 1 to 3 or a risk gradation of low, medium, or high would work, with a larger number of grades if the security measures the administrators choose to implement warrant it.
The value or sensitivity of a data asset will determine the nature of the security mechanisms administrators use to protect it. Some data types might be subject to legal or contractual compliance specifications, which impose strict limits on where and how they are stored and who can access them. The security requirements for this most sensitive data might define the highest value on the risk scale, which can call for extreme security measures such as on-premises storage in a secured datacenter, data encryption and redundancy, and highly restrictive access permissions.
Other types of sensitive data might not even be subject to broadly categorical security mechanisms, such as those applied to file folders or specific file types. Microsoft 365 includes the Azure Information Protection (AIP) tool that can apply labels to documents containing sensitive information. Administrators can configure the labels to trigger various types of security, such as watermarks, encryption, and limited access. While users and administrators can manually apply the labels to documents, AIP can also detect sensitive information in documents and automatically apply labels to them. For example, when a user creates a Word document, administrators can configure AIP to detect values that appear to be credit card numbers, as shown in Figure 3-60, and apply a label to the file that calls for a specified degree of protection.
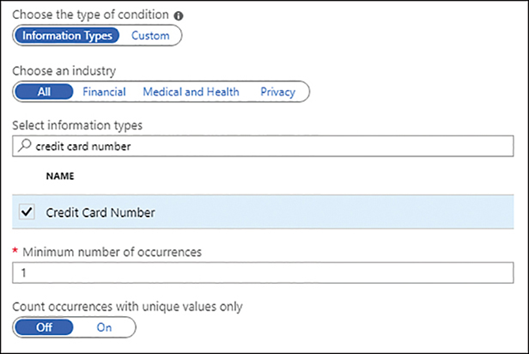
FIGURE 3-60 AIP configuration
Data that does not greatly threaten confidentiality, integrity, and availability is at the low end of the risk scale. This data will require some protection, but the security at the low end of the scale might be limited just to file system access permissions.







Leave a Reply