In recent years, there has been legislation passed in many countries providing citizens with the right to request that organizations disclose any personal information about them that they possess. These might seem like simple requests to the requestor, but for an organization that maintains a large data store, locating all of the requested information concerning a particular individual can be a difficult and time-consuming task.
Microsoft Priva aids in this process by evaluating the organization’s data and prioritizing the content for review as soon as an administrator creates a new rights request. The Subject Rights Requests overview page, shown in Figure 3-57, lists the currently in-progress requests and quantifies them by Top Request Types and Status.
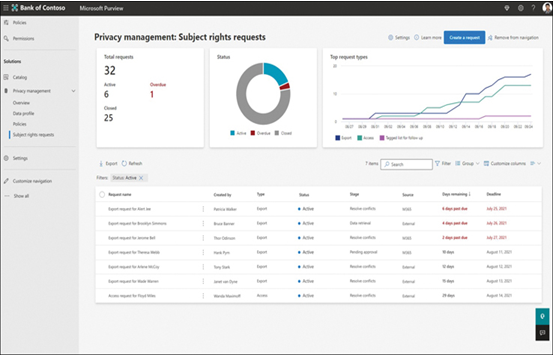
FIGURE 3-57 The Microsoft Priva Privacy Management: Subject Rights Requests page
The process by which data is evaluated and selected for inclusion in the request can be a complicated one that might involve stakeholders throughout the organization. To facilitate this process, Priva creates a Microsoft Teams channel for each request in which the personnel involved can discuss the matter.
For more information about a specific request, administrators can select an entry from the list and open a details page showing the progress of that request, as shown in Figure 3-58.
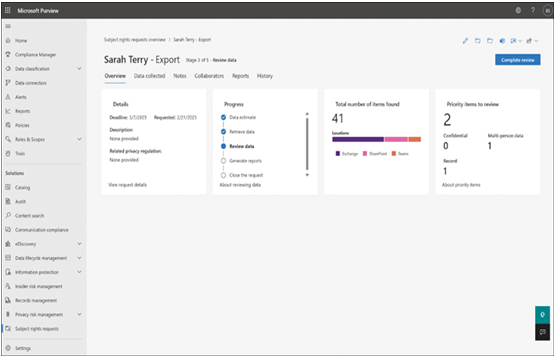
FIGURE 3-58 The detail page for a subject rights request in Microsoft Priva
After evaluating and selecting the data to be included in the request, Priva generates reports for the subject of the request and the company’s records.
Describe insider risk management solutions to protect against internal threats
Typically, information is the most valuable resource a business possesses. When considering security measures for an enterprise network, the ultimate end of these measures is to protect the information. Protection against unauthorized users or devices is really just a means of protecting the data that those users can access and store on those devices. Computers and other hardware devices have monetary value, but the physical security measures of a datacenter—for example, the electronic door locks, the security guards, and the fire suppression systems—are there primarily to protect the information stored on the hardware and not so much the hardware itself.
The process of creating a security plan for an enterprise is known as risk management, which is the act of identifying the assets that need protection, determining the potential dangers to those assets, assessing the impact of those dangers to the organization, and implementing protective measures appropriate to the assets and the threats. Microsoft 365 includes a large collection of tools that can help with all phases of this process. The security technologies in Microsoft 365 are divided into four areas, as follows:
- Security management
- Identity-based protection
- Information protection
- Threat protection
The technologies in each of these areas are shown in Figure 3-59. An organization seeking to secure its enterprise network is unlikely to need all these technologies. Consider these to be a toolkit from which administrators can select the right tool for each task. Microsoft’s Core Services and Engineering Operations (CSEO) group has chosen the technologies protruding from the wheel shown in the figure.
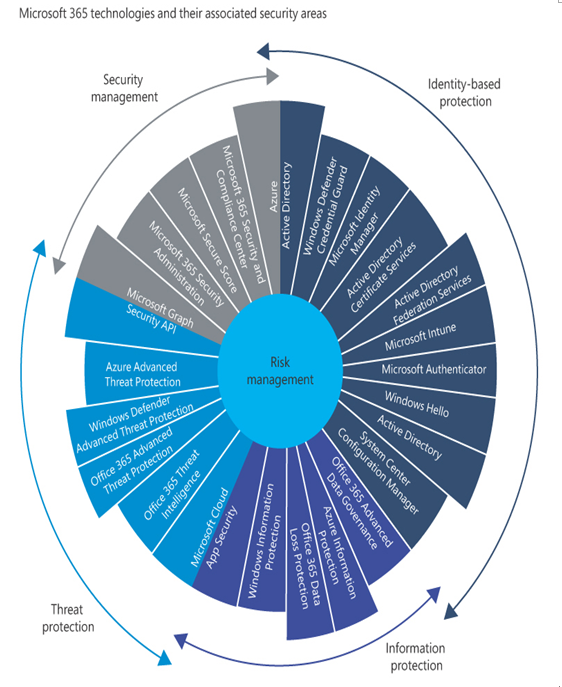
FIGURE 3-59 Microsoft 365 security technologies used by the Microsoft CSEO group
Therefore, the first step of the risk management plan is to identify the types of information the organization possesses and determine the value of each information type to the business.







Leave a Reply