At one time, enterprise network security consisted of company-owned computers (deployed and managed internally), and protected using password policies, firewalls, antivirus software, and dial-up and virtual private network connections for a few remote users. Network administrators controlled all the equipment, and a generation of Client Management Tools (CMTs) appeared, such as Microsoft’s System Center Configuration Manager (SCCM). Now part of the Microsoft Intune family of products and called just Configuration Manager, the tool provides a unified management solution that enables administrators to inventory hardware, deploy operating systems and applications, update software, manage licenses, and remotely control computers all over the enterprise.
Unfortunately, management platforms like SCCM were designed for use with on-premises computers only, and they communicate over local area networks (LANs). As mobile computing devices became increasingly common, a new management platform was needed, one that could function through the cloud. Mobile Device Management (MDM) was the first iteration of that new platform. MDM products typically exercise complete control over the mobile devices they manage, and as a result, it became common for organizations using the products to own the devices as well.
However, workers often had problems with the usability constraints imposed by company-owned, company-managed devices. These problems only became more severe as people began to purchase their own smartphones and find them easier to work with than their MDM-managed company devices. This eventually resulted in the BYOD (Bring Your Own Device) concept, which certainly pleased users but made administrators’ lives more difficult.
To provide adequate security on devices the company does not own, a new evolutionary step in the development of management products was needed, and enterprise mobility management (EMM) tools, such as Microsoft Intune, were the result. Using Intune, administrators can enroll, configure, and manage mobile devices on several different operating system platforms, wherever the devices happen to be. Administrators can even intervene when a threat to security occurs by blocking a device’s access to the company network and erasing any sensitive information stored on it.
However, despite the advances in mobile computing and mobile device management, on-premises devices, applications, and services have not gone away and still need to be managed. CMTs and EMMs are different types of management platforms in many fundamental ways. Both require administrators to have significant training and experience, but the two generally do not overlap. A need arose for a management platform that could work with both on-premises and cloud-based devices, as shown in Figure 3-32; this management platform also needs to be extendable to include new technologies as they develop, such as wearables and the Internet of Things (IoT). This new platform has come to be known as unified endpoint management (UEM).
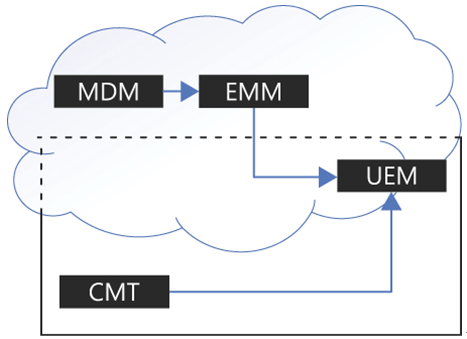
FIGURE 3-32 Development of Unified Endpoint Management
The term endpoint has come to be used to refer to any user device, including desktop computers, laptops, printers, tablets, smartphones, and newer technologies, such as wearables and Internet of Things devices. Unified endpoint management aims to eliminate the need for separate management tools for on-premises and mobile devices. An ideal UEM solution is a “single-pane” administration platform that can manage the applications, identities, resources, updates, security, and policy compliance for all the endpoints in the enterprise, regardless of their locations, device types, or operating systems.
Note Internet of Things
As mobile networking moves beyond the now ubiquitous smartphone, the next evolution appears to be the Internet of Things (IoT), in which mobile computing devices are embedded in various types of tools, appliances, and systems. Home and building automation is a growing market for IoT devices, including thermostats, light switches, refrigerators, and large-scale industrial and utility systems.
In the healthcare industry, IoT devices—including heart rate, blood pressure, and blood glucose monitors—can monitor patients’ conditions both inside and outside hospitals; also, they can control implanted devices, such as pacemakers and defibrillators. Automobiles and other vehicles are also common applications for IoT, which can provide location monitoring, toll collection, and traffic control services.
All these device types require management by network administrators and could conceivably be as much of a security threat as any of the other mobile computing devices in use today. For example, one can only imagine the chaos if an attacker managed to penetrate a hospital network or a city’s power grid.







Leave a Reply