All identities are a potential source of risk for the entire network, no matter what level of privileges they possess. Once attackers compromise one identity, it becomes relatively easy to spread laterally within the enterprise and compromise others. Therefore, administrators should try to protect all identities, not just the ones with administrative privileges.
One of the key innovations of Microsoft 365 is the greater emphasis on proactive threat detection and remediation. Microsoft Entra ID (formerly Azure AD) can provide this type of security for user accounts with a feature called Microsoft Entra ID Protection. Identity Protection evaluates the sign-in activities of individual user accounts and assigns risk levels that increment when multiple negative events occur. There are two risk levels associated with each identity, as follows:
- Sign-in risk The probability that an unauthorized individual is attempting to authenticate with another person’s identity
- User risk An accumulated probability that a specific identity has been compromised
Microsoft Entra ID Protection recognizes the following risk events and modifies an identity’s two risk levels based on the order and frequency in which they occur:
- Atypical travel The user signs in from an atypical location for the user or is geographically impossible based on the user’s other recent sign-ins. Microsoft Entra ID takes into account the travel time between the locations and gradually develops its own profile of the user’s habits, which helps to prevent the occurrence of false positives (that is, conclusions of risk from sign-in patterns that are common for that user).
- Anonymous IP address The user signs in from a browser that suppresses the user’s IP address, such as Tor or a virtual private network (VPN) client. The user signing on might or might not be the identity owner, but Entra ID considers the anonymity to be suspicious.
- Unfamiliar sign-in properties The user signs in from a client with unfamiliar properties, such as a new location, an unusual IP address, or an autonomous system number (ASN), based on the user’s previous activities. For new identities, there is a period of information gathering that lasts at least five days, during which Entra ID makes no risk assessments using this criterion.
- Malware-linked IP address An identity is associated with an IP address previously used to contact a known bot server on the Internet. The system is then assumed to be infected with malware and considered to be a risk.
- Leaked credentials An identity is determined to use credentials known to have been compromised. Microsoft gathers information about such credentials from numerous sources, including law enforcement agencies, security consultants, and illicit websites.
When these events occur, Entra ID evaluates them and modifies the behavior of the authentication process according to criteria established by administrators. There are obviously many possible combinations of behaviors that Entra ID might have to take into account when evaluating the risk levels of an identity. For example, if the same risk events occur repeatedly, the risk levels will continue to rise until a drastic reaction, such as blocking all access to the identity, might be required.
The basic Azure AD Identity Protection process is illustrated in Figure 3-31.
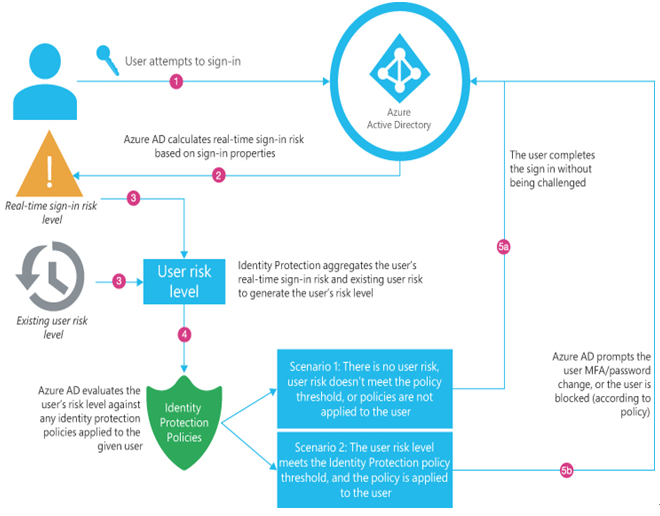
FIGURE 3-31 The Azure AD (Entra ID) Identity Protection risk evaluation process
For example, when a user attempts to sign in with a simple password from an anonymous IP address, Entra ID determines that it is a risk and assigns it a sign-in risk level of medium. This risk level causes Entra ID to implement a Conditional Access policy that imposes a specific action, such as requiring multifactor authentication during the sign-in process. If the user successfully completes the multifactor authentication, the user risk level remains unchanged.
However, if the user fails to complete the multifactor authentication, Entra ID considers this to be a possible indication that the identity has been compromised and raises the user risk level. The next time the user attempts to sign on, the process might proceed completely normally, with no sign-in risk detected; however, the user risk level associated with the identity persists, and Entra ID might be configured to prompt the user to change the password.
Entra ID Protection is included only with the Entra ID P2 (formerly Azure Active Directory Premium P2) plan, supplied with the Microsoft 365 Enterprise E5 edition.
Exam Tip
The additional security provided by Azure AD Identity Protection applies only to cloud-based identities, not the on-premises identities in Active Directory Domain Services. Microsoft’s increased emphasis on cloud-based solutions, such as Microsoft 365, means that the latest innovations in security and other areas are not being ported to the traditional on-premises versions. For this reason, Microsoft recommends that enterprise networks shift more of their applications and services away from on-premises servers and into the cloud. When preparing for the MS-900 examination, candidates should be conscious of this emphasis on the cloud and carefully distinguish Microsoft’s cloud-based products from its on-premises products.







Leave a Reply