The something you are is usually some type of biometric scan. The Windows Hello for Business feature in Windows 10 and 11 supports multifactor authentication with biometric scans as one of the factors. It is also possible to use the Microsoft Authenticator app for mobile devices as a biometric scanner that enables users to access Microsoft 365 resources with no password.
Fingerprint readers are inexpensive and an increasingly common feature on laptops and other mobile devices. There are also aftermarket keyboards for desktop computers with integrated fingerprint readers as well. Fingerprint scans do not provide impenetrable security; fingerprints can conceivably be duplicated, and a scan of a finger would presumably still work, even if it was not attached to its owner. However, in combination with a password, fingerprint scans provide a multifactor authentication solution that usually cannot be penetrated casually.
Facial recognition is another type of biometric scan that Windows Hello can use for multifactor authentication. Cameras are all but ubiquitous in modern society, so it would seem that the hardware costs of a facial recognition system are minimal. This is not the case, however, at least with Microsoft’s facial recognition products. Facial recognition raises questions both of security and of privacy. If a computer can recognize a person’s face as a security factor, what would stop an intruder from holding up a picture of the person to the camera? And where is the image of the user’s face being sent to accomplish the authentication?
Microsoft has answers to both questions. Windows Hello for Business supports the use of facial recognition for user authentication, but it requires a camera with a separate infrared light source and a near-infrared sensor. The main problem with facial recognition systems on personal devices is that people can conceivably use them in any kind of lighting. Near-infrared imaging provides a consistent image regardless of the visible light conditions. Windows Hello also does not store images of the user’s face and never transmits them to other locations for authentication. When a user enrolls in Windows Hello, the Windows Biometric Framework processes a facial image within the device and stores it as an enrollment profile. The system performs the same process in subsequent authentication attempts and compares the results to the profile.
Something you have
While the something you have in multifactor authentication can be a smart card or some other form of identification, in Microsoft 365, it is usually a cell phone. This is a more practical option because most people today carry cell phones with them, whereas card readers are far less common.
Internet websites commonly require a secondary authentication factor, usually in the form of a code (called a one-time password or OTP) sent to the user’s cell phone as a call or SMS text. The user supplies the code from the website, and authorization is granted. Microsoft 365 supports this method for multifactor authentication of users’ Entra ID identities, among others.
The cellphone-based options for Entra ID Multifactor Authentication (MFA) are as follows:
- SMS Text Of OTP Code To Mobile Phone After the user completes a standard password authentication, Entra ID sends a text message containing an OTP code to the user’s preconfigured telephone number. The user types the code into the sign-in screen to complete the authentication.
- Automated Voice Call To Mobile Phone After the user completes the password authentication, Entra ID generates an automated voice call to the user’s preconfigured telephone number. The user answers the call and presses the phone’s # key to complete the authentication.
- Notification To Mobile App After the user completes the password authentication, Entra ID sends a notification to the Microsoft Authenticator app on the user’s smartphone. The user taps the Verify button in the app to complete the authentication.
- Verification Code In Mobile App The Microsoft Authenticator app generates a new open authentication (OATH) verification code every 30 seconds. After the user completes the password authentication, the user types the current verification code from the Microsoft Authenticator app into the sign-in screen to complete the authentication.
Of course, cell phones can be lost, stolen, or destroyed, so any authentication method that relies on them will not be completely secure, but in combination with a password, they provide a significant barrier against the standard attacker. Multifactor authentication is not required for Microsoft 365, but it is a de facto standard for network security today, largely because many administrators are finding that they have reached the limits of their password authentication policy effectiveness as far as users’ tolerance is concerned.
Administrators can enable multifactor authentication for specific users using the multifactor authentication screen in the Microsoft Entra admin center, as shown in Figure 3-12.
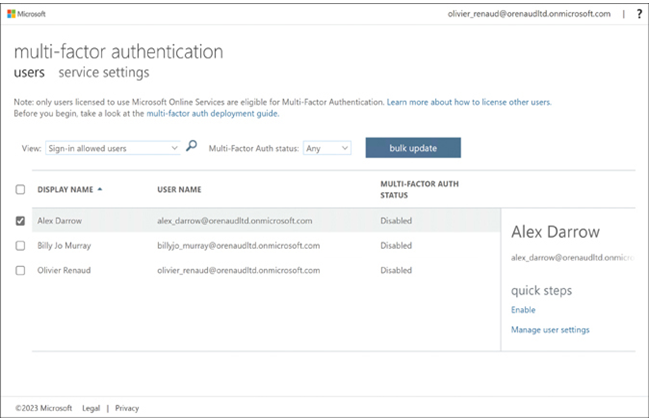
FIGURE 3-12 The Multi-factor Authentication screen in the Microsoft Entra admin center
The next time users sign in, a screen like that shown in Figure 3-13 enables them to enter a phone number and specify whether the initial contact to a user should be through a code sent to the user’s cell phone or a mobile app, such as Microsoft Authenticator.
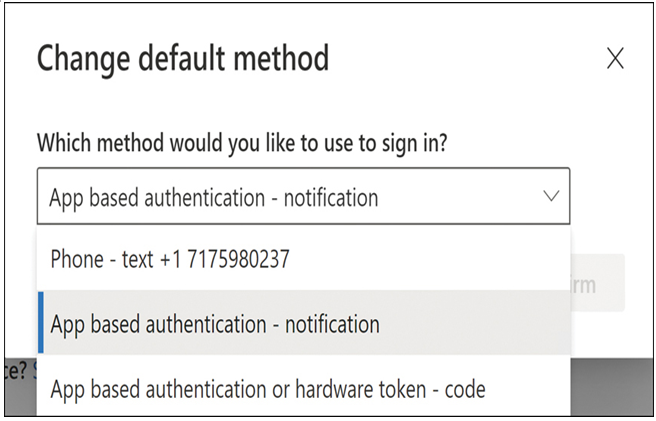
FIGURE 3-13 The Change Default Method dialog box







Leave a Reply